- Published on
0xL4ughctf 2024 - Wordpress 2
- Authors

- Name
- Lumy
Wordpress 2
Q1. During enumeration, the attacker tried to identify users on the site. List all the users that the attacker enumerated. (seperate them with 3), (sort them by alphapitical order)
Q2. After enumeration, a brute force attack was launched against all users. The attacker successfully gained access to one of the accounts.What are the username and password for that account, and what is the name of the page used for the brute force attack?
Flag Format
OxL4ugh{A1_A2}Example:0xL4ugh{username1:username2_username:password_pageName.ext}
Table of Contents
Source
The challenge gives us a pcap file : Wordpress.pcapng
Solution
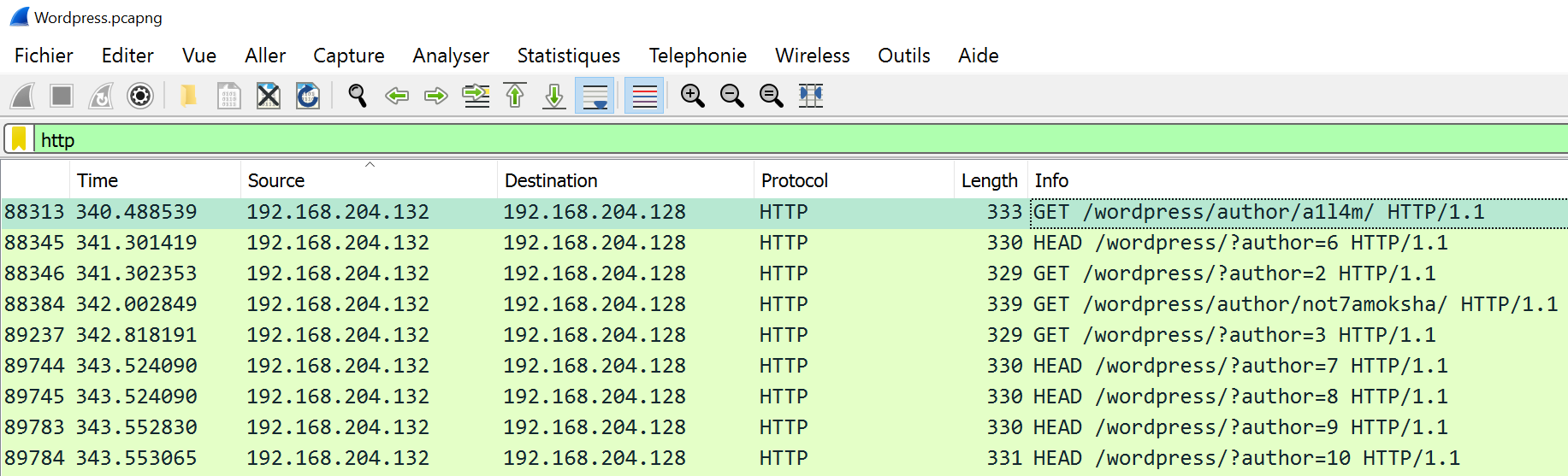
Let's see which what are the users that has been bruteforced. For that we can see the endpoint /wordpress/author/XXX
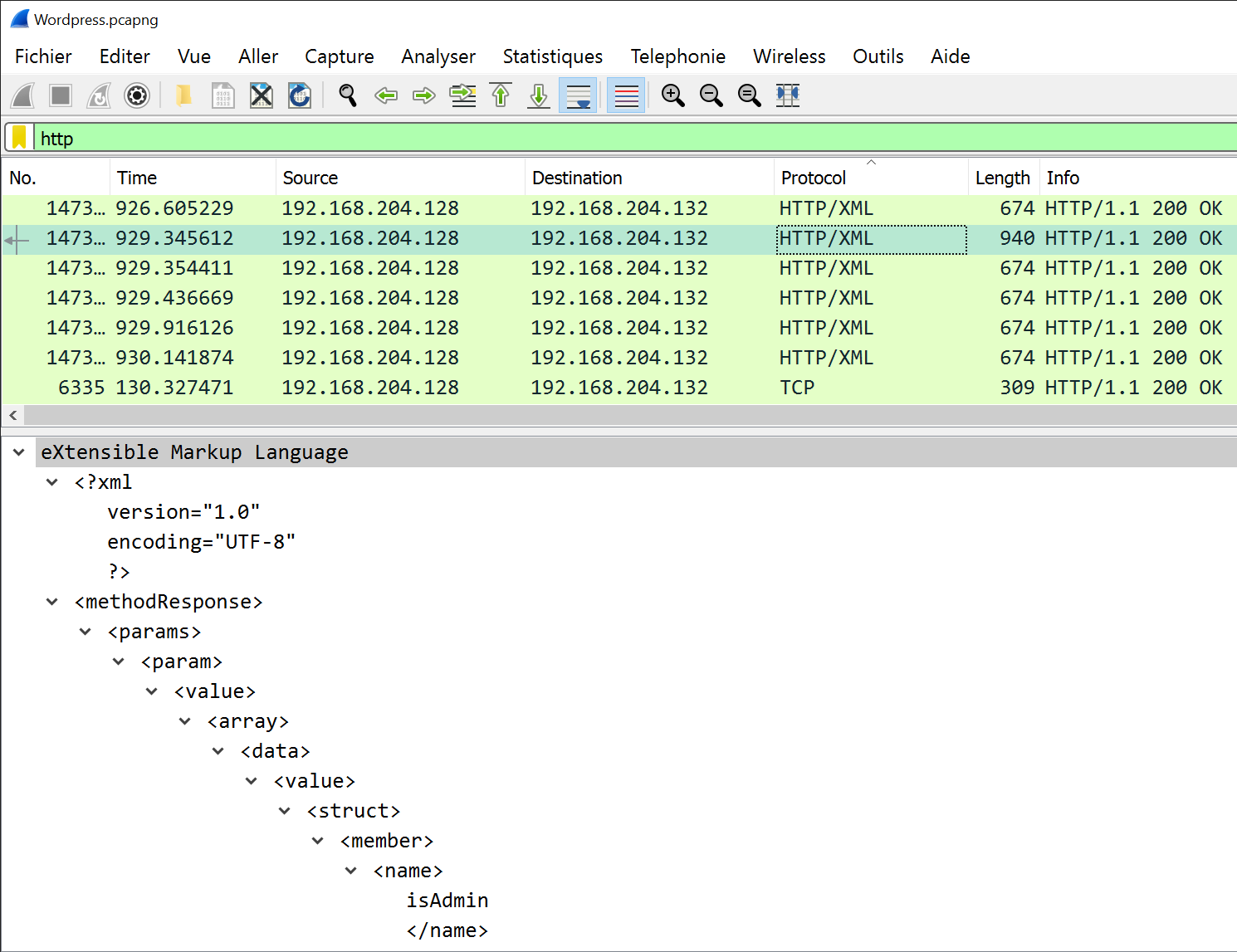
To gather the password bruteforced, we can see an XMLRPC request with an odd length, containing the isAdmin variable
Finally, we can thus gather the initial attacker request for this response by following HTTP request
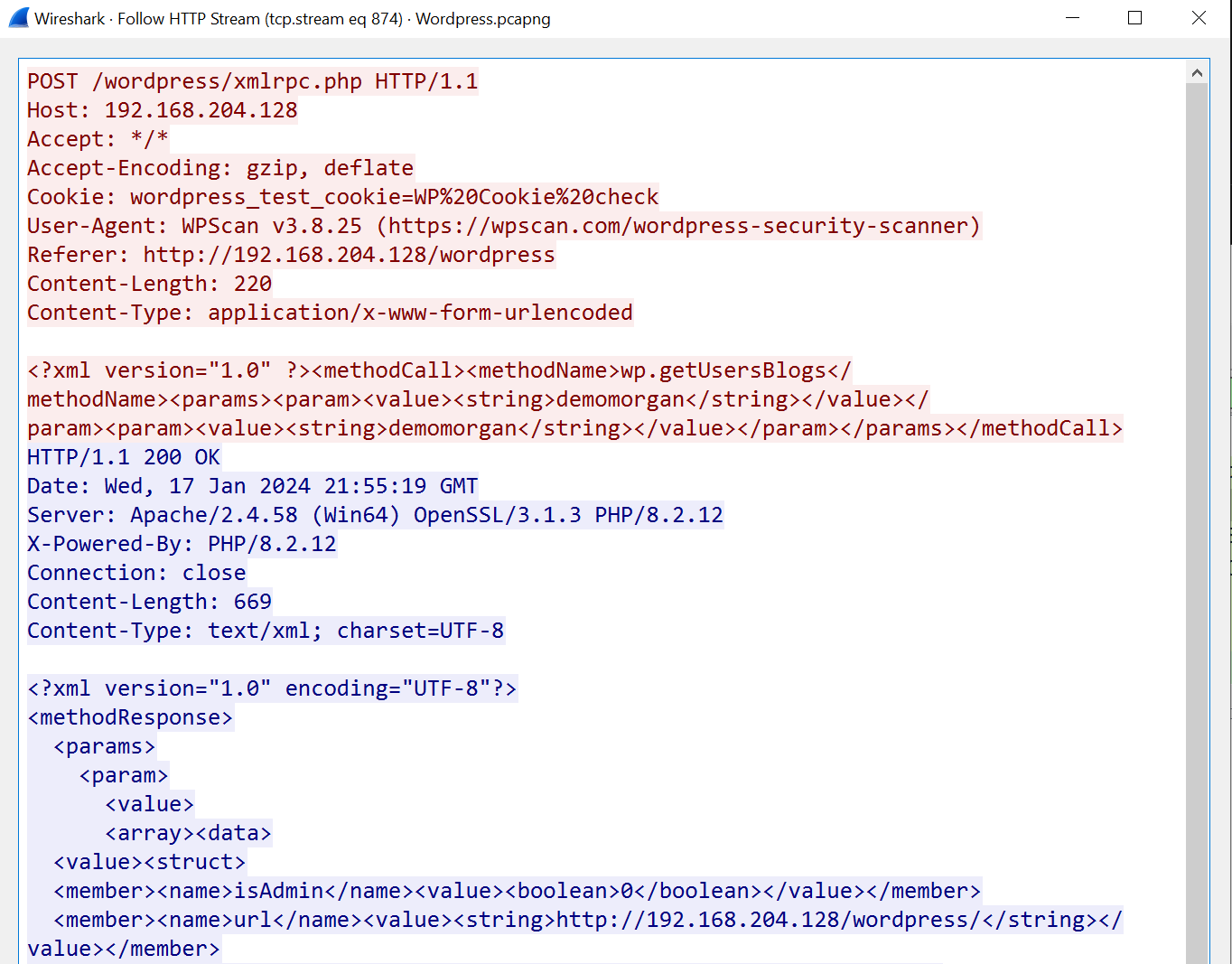
Flag : 0xL4ugh{a1l4m:demomorgan:not7amoksha_demomorgan:demomorgan_xmlrpc.php}